Introduction
Understanding what is going on with your computer’s network is crucial. You may need to monitor active connections to ensure they are legitimate. For example, if your PC is overwhelmed by a malicious connection, it is essential to track and identify the source to disconnect it and protect your system.
You will learn about network sessions and how they are handled by computers, understand the differences between some networking terms, and discover how to monitor active connections on your computer at any point in time. You will be equipped with a powerful and easily accessible utility called netstat.
Table of Contents
Understanding Network Session, Socket, and Endpoint
For any host to communicate or send a message to another host on a network, it must have a network session with the intended host to enable the exchange of data. This session information helps both parties determine where to send or receive data. The network can be a LAN or WAN or any other type of network.
Let’s clarify some confusing networking terms simply and clearly:
- A session is any single communication between two hosts.
The term session refers to the entire connection or interaction between the hosts. For example, if you are having a conversation with a friend sitting in front of you, that communication or connection is considered a session.
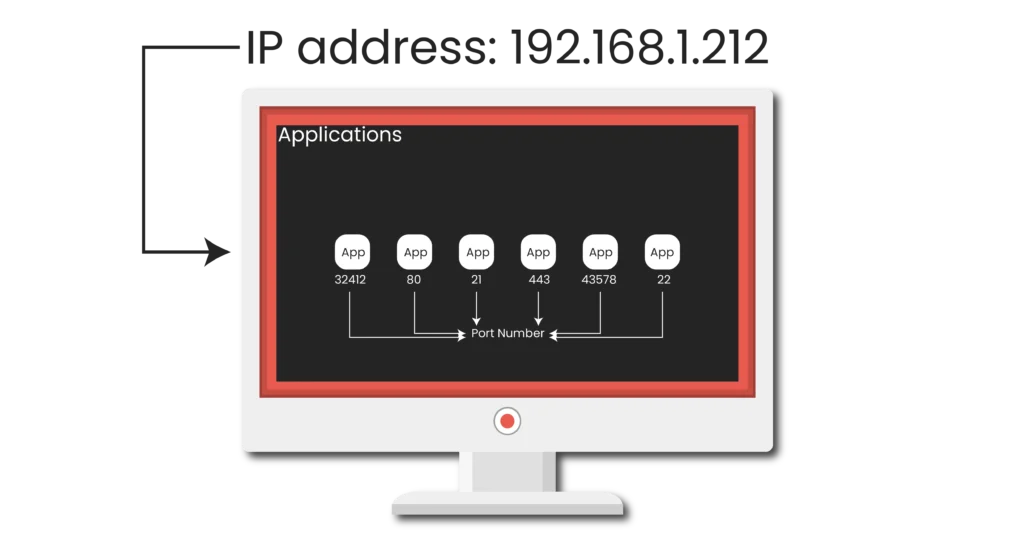
- A socket, or endpoint, represents the session information on one host. It is a combination of an IP address, a port number, and a Layer 4 protocol–either TCP or UDP. This information is stored in memory on the host.
Layer 4 here refers to the Transport layer of the OSI seven-layer Model. You can learn more about the Transport layer here.
Both communicating parties have session information about the same connection. The two hosts involved in the communication must keep track of the communication status.
- A socket pair, or endpoints, represents the session information stored in memory on two hosts about the same connection.
As two hosts begin to communicate over the network, they store information about the session. Do you know what this information is called? you guessed it–it is called the endpoints.

Introducing the netstat utility
netstat stands for network statistics. It is a command-line utility that displays protocol statistics, listening ports, and active TCP/IP connections that occurring at any given time. It provides statistics for various protocols, including IPv4, IPv6, ICMP, ICMPv6, TCP, TCPv6, UDP, and UDPv6.
netstat is available on various operating systems, though the output and options may vary slightly between them.
Now that we have an understanding of network sessions and their associated information. Let’s see netstat in action.
Using netstat to Reveal Active Sessions
In this section, I will focus on using netstat in the Microsoft Windows 10 operating system.
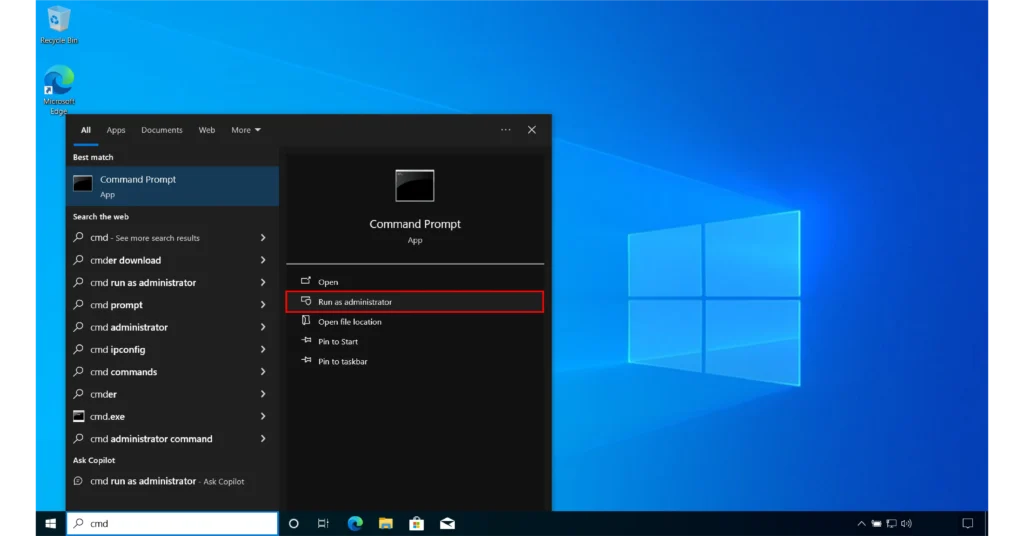
Since netstat is a command-line utility, you need to open a command prompt. Type cmd in the search bar and select “Run as Administrator”, as some options you will use later require Administrator privileges.
Most netstat Options
netstat offers a range of switches to customize and display different types of network information.
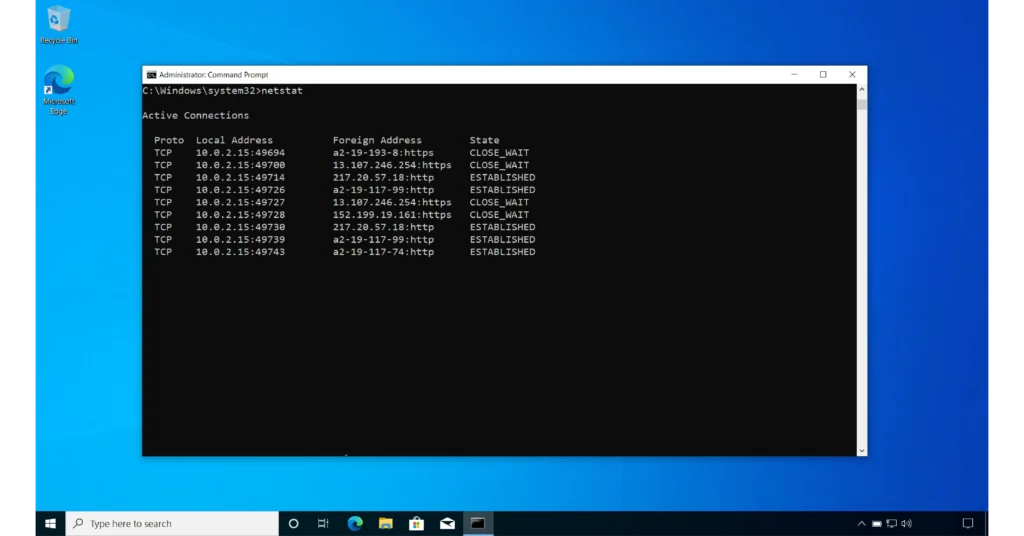
1- With No Switches
netstatBy default, without any switches, netstat displays the current active TCP sessions on your computer. The output is organized into a table with four columns, listing each session along with its relevant information.
The output may take some time to process, as netstat attempts to resolve IP addresses to hostnames using DNS, and also translates port numbers into their corresponding protocol names. For example, instead of displaying an IP address and the HTTPS port number (443) directly, netstat may show a hostname along with “https” separated by a colon.
Press CTRL + C, if you want to stop the output.
The first column, labeled “Proto”, lists the Layer 4 protocol used in each session. The second column, labeled “Local Address”, lists the local machine’s IP address and the port number associated with each session. The third column, labeled “Foreign Address”, lists the remote machine’s IP address and port number associated with each session. Finally, the fourth column, labeled “State”, indicates the connection status.
Every row represents a session. The combination of the Layer 4 protocol and the Local Address column of each row represents the local machine’s socket, while the combination of the layer 4 protocol and the Foreign Address column of each row represents the remote machine’s socket.
2- With -a Switch
The -a switch instructs netstat to display all active connections and listening ports.
netstat -a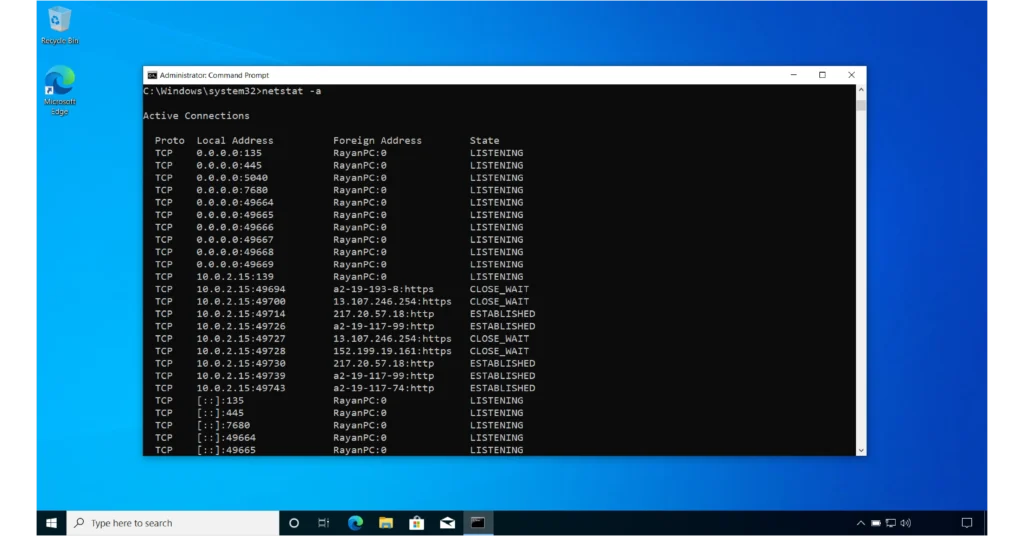
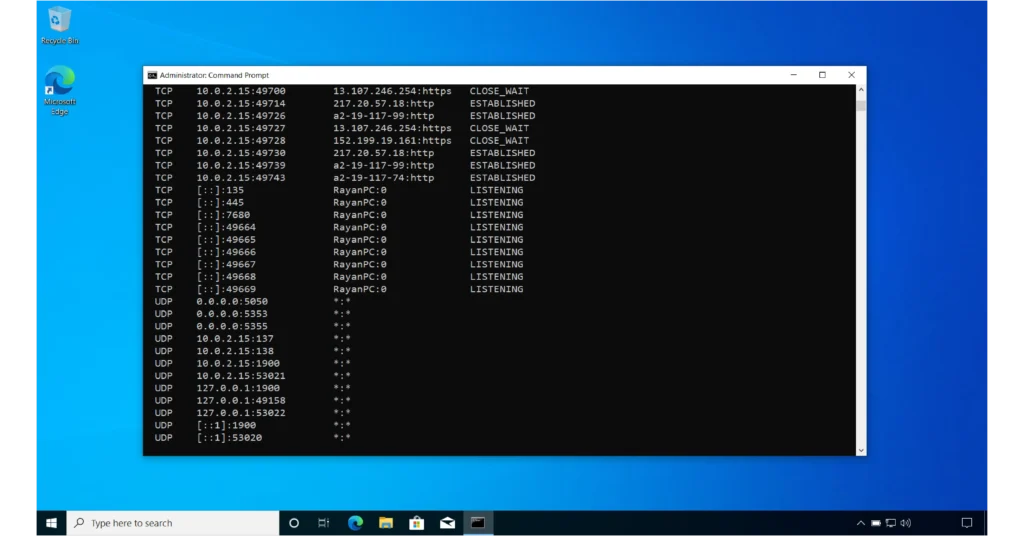
I have included two images above to show you a complete example.
Let me explain some aspects that might seem strange.
- Listening or open ports refer to sockets that are ready to respond to any incoming traffic directed to their specific port number.
- Focusing on the first line in the table, specifically on
0.0.0.0:135, the IPv4 address0.0.0.0indicates that port number135is active on all Network Interface Cards (NICs) on this PC. This means that any incoming requests destined for port 135, regardless of which NIC they arrive on, will be accepted and processed. Even if you have only one NIC, Windows displays it this way.
- In IPv6 (Internet Protocol version 6), the address
::represents a series of zeroes. This notation is a shorthand for the full address0000:0000:0000:0000:0000:0000:0000:0000, where::denotes the presence of multiple consecutive zero fields. This is equivalent to the IPv4 address0.0.0.0as previously explained.
- Port
0is a reserved TCP/IP port number that instructs the operating system to automatically select an ephemeral, system-allocated port number.
- In the output of this example, some rows list the Foreign IP address as “RayanPC”, which is my PC’s name resolved using DNS.
- In IPv6, the address
::1is the loopback address, which is equivalent to the IPv4 loopback address127.0.0.1.
- An asterisk
*in netstat means “Any”. In the context of*:*, the first asterisk*means that connections can come from any IP address, while the second asterisk*, in*:*, signifies that connections can originate from any port number on the remote machine.
IP addresses identify the machine itself, while port numbers specify the applications running on that machine. Port numbers operate at the Trasnport layer of the OSI seven-layer model.
3- With -n Switch
The -n switch instructs netstat to display port numbers and IP addresses in numerical form rather than resolving them to names. For example, it shows port 443 as a number rather than translating it to “https”.
netstat -n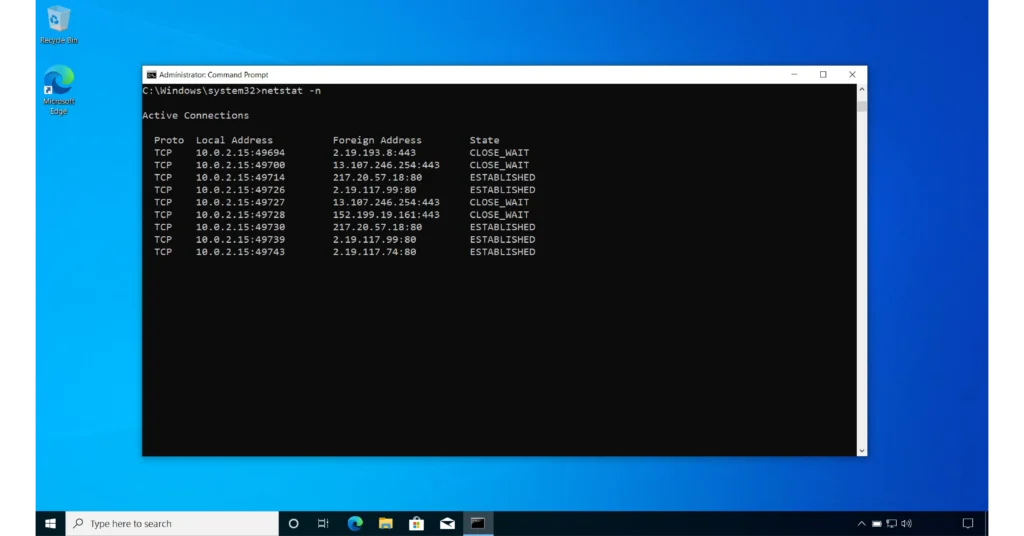
Notice the port numbers 443 for HTTPS and 80 for HTTP are displayed in numerical form.
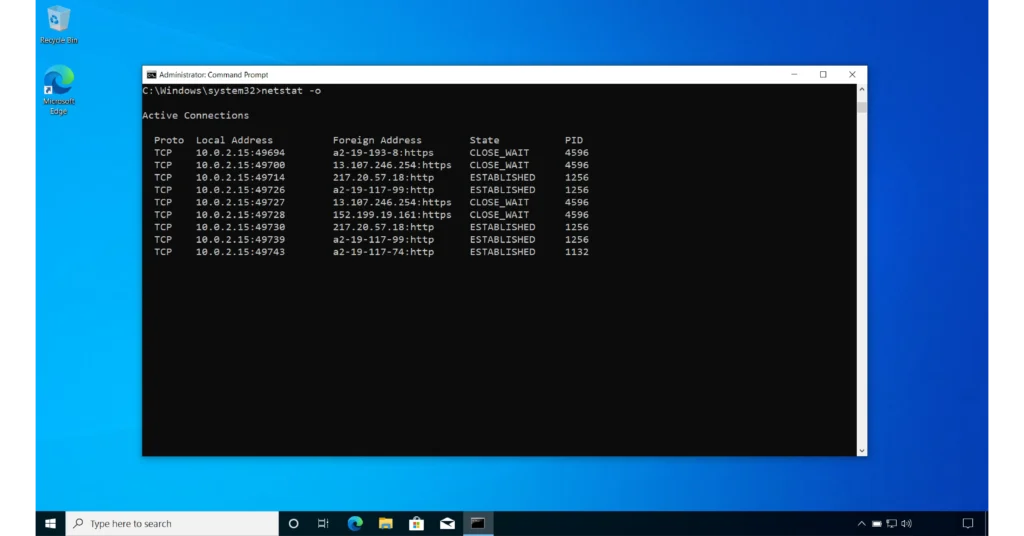
4- With -o Switch
The -o switch instructs netstat to display the process ID (PID) associated with each session. Every process running on a computer is assigned a unique process ID, which the operating system uses to track and manage processes.
netstat -oA new column, labeled “PID” (Process ID), will be added.
5- With -f Switch
The -f switch instructs netstat to display fully qualified domain names (FQDNs). An FQDN includes both the domain name and the hostname. For example, if your domain name is “something.com” and you have a Web server named “web”, the FQDN for the Web server would be “web.something.com”.
netstat -f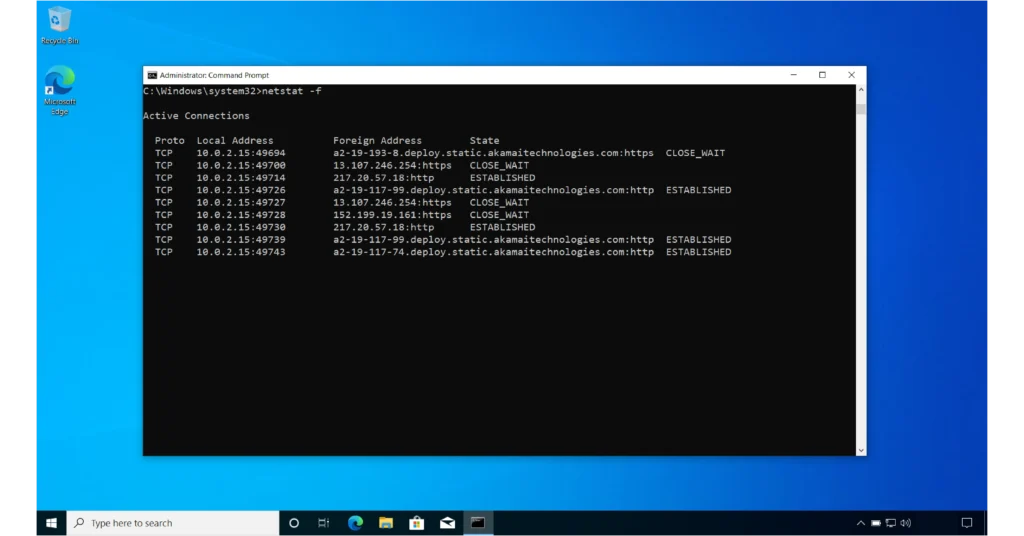
6- With -b Switch
The -b switch instructs netstat to display the process name associated with each session. Note that this switch requires elevated privileges, meaning you need Administrator rights to run it.
netstat -b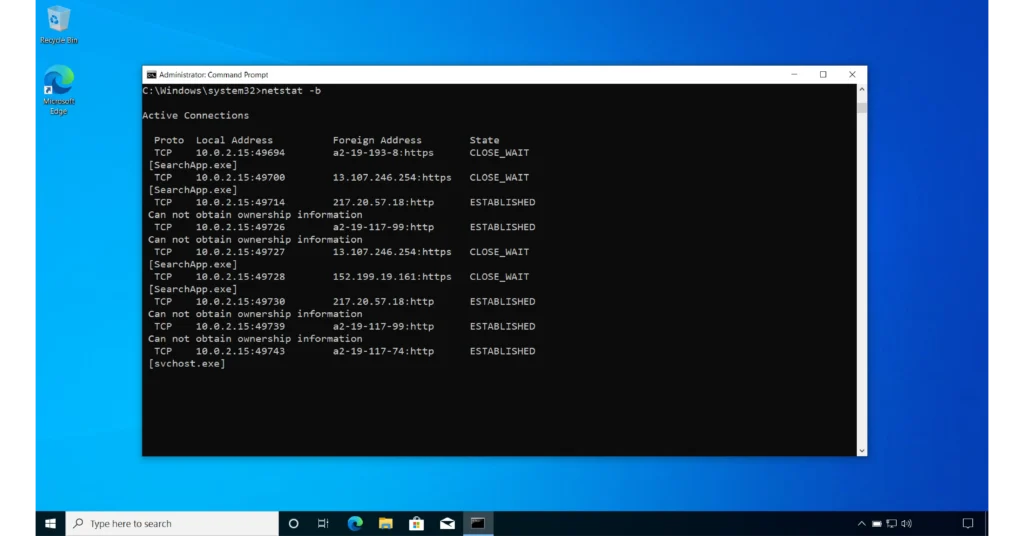
If a process name is not shown, use the -o switch to display the process ID (PID). Then, open Windows Task Manager to identify the process by its PID in the Details tab. You can access Task Manger using the shortcut CTRL + SHIFT + ESC, or by typing its name in the search bar.
7- With -p Switch
The -p switch instructs netstat to display sessions for specific protocols. It is followed by the protocol name, such as:
netstat -p tcp8- With -r Switch
One of the more interesting switches is the -r switch, which instructs netstat to display all available network interfaces along with their MAC (physical) addresses, as well as the IPv4 and IPv6 routing tables.
netstat -r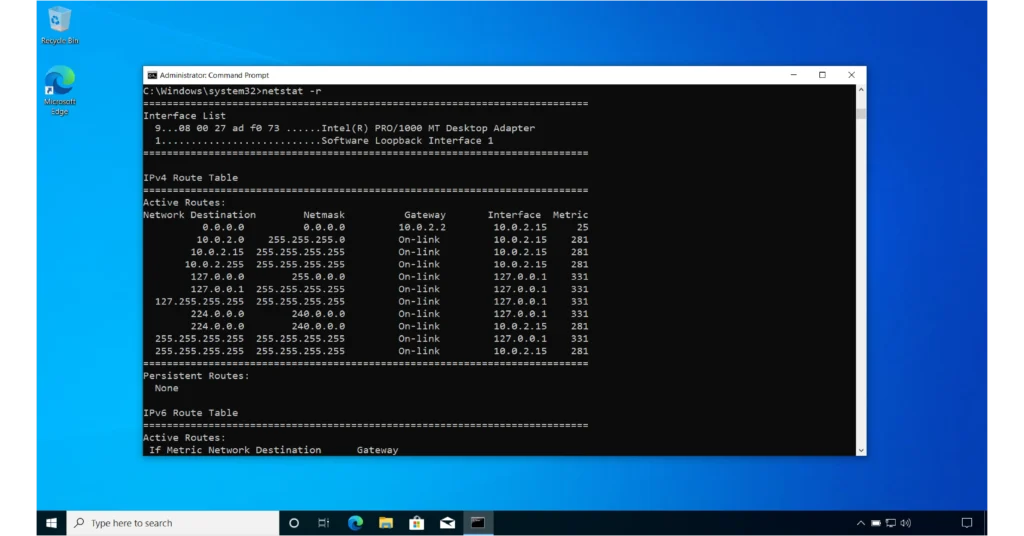
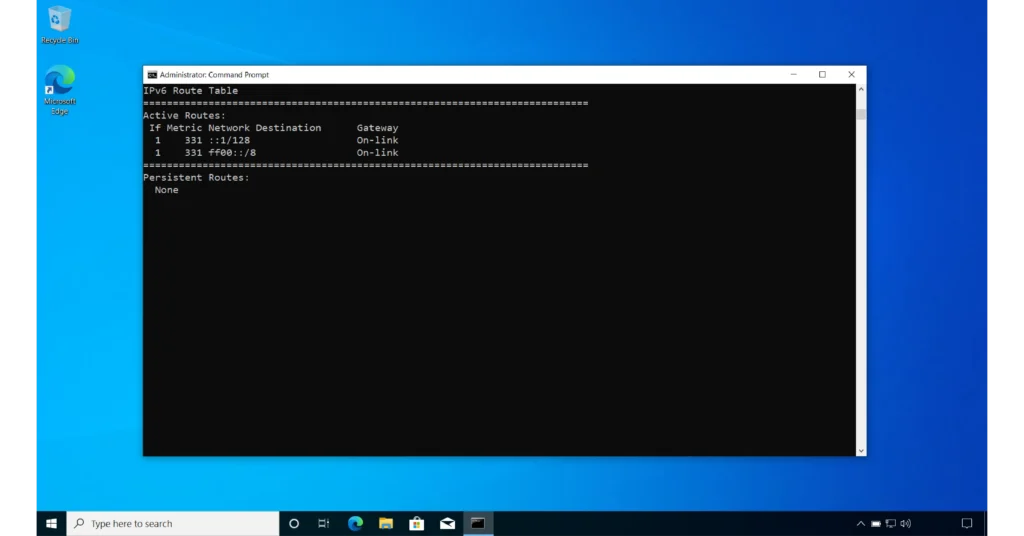
I have included two images above to show you a complete example.
9- With -s and -e Switches
The -s switch instructs netstat to display protocol statistics, including IPv4, IPv6, ICMP, ICMPv6, TCP, TCPv6, UDP, and UDPv6.
The -e switch instructs netstat to display Ethernet statistics.
Explore the output and delve into the details yourself.
10- Combining Switches
Most importantly, you can combine switches together with a single hyphen at the beginning. Combining switches make netstat more powerful and informative.
Here are some examples you can discover their output on your own:
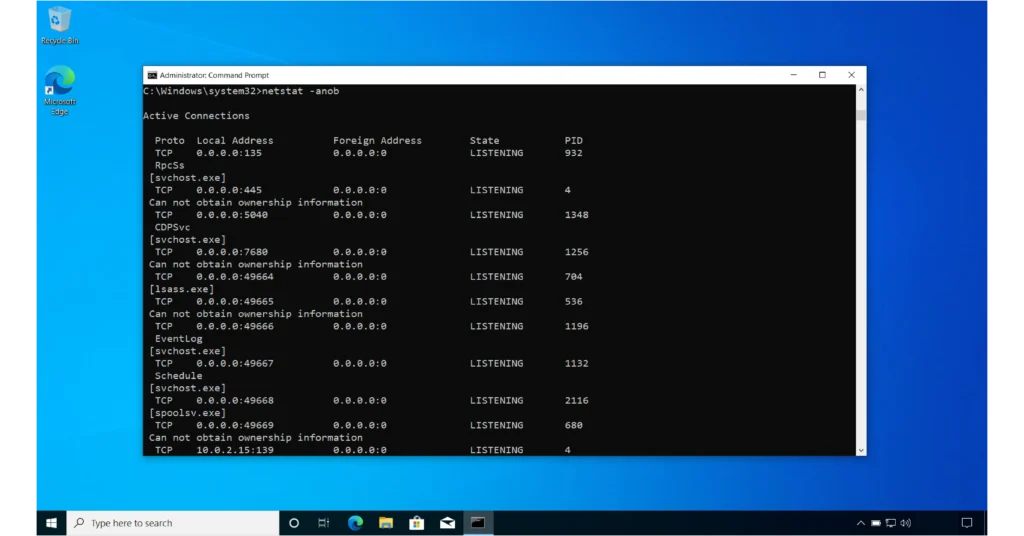
- netstat -anob (as shown in the following image). It displays all active connections and listening ports, including process IDs and names. It also lists all IP addresses and port numbers in numerical form.
- netstat -ap udp
- netstat -af
- netstat -anb
- netstat -sp tcpv6
- netstat -sp icmpv6
To view the manual for netstat, which lists its functions and all available options, use the command:
netstat /?Determining Good vs. Malicious Sessions
It involves several steps:
- Familiarize yourself with common port numbers: Memorize common TCP/IP application ports to identify the role of each session on your computer.
- Use netstat with key switches: Practice using netstat with its various switches, especially the -b and -o switches, to reveal process names and IDs.
- Understand your common operating system’s processes: Take the time to familiarize yourself with the ports and processes that typically run on your operating system.
- Check process IDs: If no process name is shown, track the process ID using Windows Task Manger or another Process Explorer. Open Task Manager easily using the shortcut: CTRL + SHIFT + ESC or by typing its name in the search bar. Then, go to the Details tab to view processes, their IDs, and additional information.
- Investigate unknown processes: If you encounter an unfamiliar process, search for its name online to figure out what it does. Many websites provide information about unknown processes.
- Remove any malicious processes.
Additional Resources
- If you want to learn more about netstat in Windows systems, check out this Microsoft article.
- For those who prefer a GUI tool, you can download and use the powerful and free tool TCPView from Microsoft developed by Mark Russinovich of Sysinternals. You can also explore more about Sysinternals here.
Conclusion
- Key networking terms:
- A session refers to the connection between two hosts.
- A socket, or endpoint, refers to the session information stored in memory on one host.
- A socket pair, or endpoints, refers to the session information stored in memory on two hosts about the same connection.
- With netstat, you can know a lot about active connections, listening ports, and protocol statistics on your computer.
- To distinguish between legitimate and malicious connections, monitor active connections and track them by Process ID and name. Research any unfamiliar process names to verify their legitimacy. If you identify malicious processes, take steps to remove them.
- Most netstat options summary:





